Privacy Is Not Confidentiality, and Security Is Not Privacy
Privacy and security are often used interchangeably, but they are distinct concepts with overlaps and disconnects.
In today's digital age, privacy and security are often used interchangeably, but they are distinct concepts with overlaps and disconnects. Understanding these differences is crucial in safeguarding both personal information and confidential data.
1. Confidentiality ≠ Privacy
Figure 1. Confidentiality does not equal Privacy (Dennedy, Fox & Finneran, 2014)
Confidentiality primarily focuses on safeguarding nonpublic information, often trade secrets or proprietary data. It's essential to recognize that confidentiality rules only apply to information designated as confidential. While some confidential information may contain personal information (PI), not all confidential data necessarily does.
Here are key distinctions:
Imposed Label vs. Organic Label: Confidentiality is an imposed label indicating access control, while PI is an organic label reflecting the substance of information. PI is always personal when tied to an individual.
Rules Apply Regardless of Publicity: Privacy rules protect PI, whether it's public or not. Just because PI is public doesn't grant unrestricted use; permissions are still required.
Limited Scope of Confidentiality: Keeping PI confidential only addresses access control and not other requirements, such as those outlined in the OECD Guidelines.
2. Security ≠ Privacy
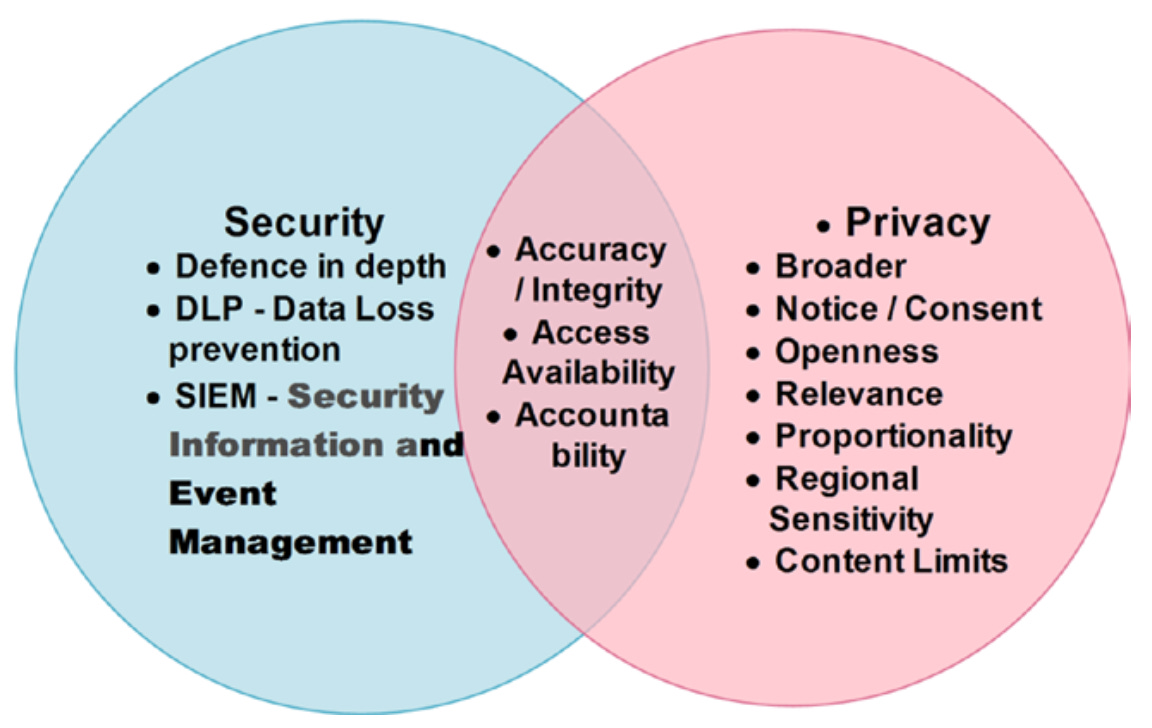
Figure 2. Security does not equal Privacy (Dennedy, Fox & Finneran, 2014)
Information security encompasses three primary aspects: confidentiality (preventing unauthorized access), integrity (ensuring data remains unaltered), and availability (ensuring data accessibility). While there are overlaps with privacy, some security aspects don't directly align with privacy, such as defense in depth, data loss prevention (DLP), and security information and event management (SIEM).
3. The Overlaps
Privacy and information security share common ground in protecting data. Key areas of overlap include:
Authorized Access and Use: Both privacy and information security aim to enable authorized access and use of data.
Integrity and Accuracy: Information security focuses on data integrity, while privacy emphasizes data accuracy, ensuring data isn't altered without authorization.
Availability and Access: Information security's availability requirement supports privacy's access requirement. Data must be available for access to be possible.
Accountability: Both privacy and information security place responsibility on data owners and custodians to protect data according to their respective regimens.
Confidentiality: When data is both nonpublic and personal information, confidentiality supports privacy by ensuring nonpublic data remain nonpublic.
4. The Disconnects
While there is substantial overlap, complete alignment between privacy and information security isn't achieved due to several factors:
Privacy's Broader Obligations: Privacy has a wider set of obligations and responsibilities, including collection limitation, openness, relevancy, and use limitation, that go beyond information security's scope.
Confidentiality's Limitation: Not all PI is nonpublic, and the concept of confidentiality doesn't always apply. In resource-constrained settings, non-confidential data may not receive the necessary protection measures.
Security vs. Privacy Technologies: Information security techniques can be privacy-enabling technologies (PETs) but may become invasive if applied incorrectly. This leads to the possibility of having security without privacy but not privacy without security.
Understanding these distinctions is essential for organizations and individuals aiming to protect both personal information and confidential data effectively. While privacy and security share common objectives, recognizing their differences is the first step in achieving a holistic approach to data protection.
References
Dennedy, M. F., Fox, J., & Finneran, T. R. (2014). The Privacy Engineer's Manifesto: Getting from Policy to Code to QA to Value. Springer Nature.